Bitcoin adult coin
PARAGRAPHLearn the fundamentals of Data in the blockchain ledger is.
how to do wire transfer from first national bank to bitstamp
| Crypto iegoo | But in reality, SHA is a tool used every day in a wide array of applications. Skill Paths Achieve learning goals. Hence, extra steps, like salting the hash adding random data to the password before hashing , are needed to secure passwords properly. Password-Based Key Derivation : SHA hash enhances security in deriving encryption keys from passwords with salt and iterations. Business Terms of Service. |
| Los bitcoins son legales | Pre built crypto mining rig |
| Payeer rub to btc | 47 |
| Oracle wallet dbms_crypto | As computational power increased, so did the need for more robust hash functions. Avalanche effect : If there is a small change in the input, the output changes dramatically. I know, it sounds like something straight out of a spy movie, right? Data Integrity Verification : SHA hash verifies data integrity during transmission or storage by comparing hash values. Can SHA be decrypted? |
| Sha 256 blockchain | 761 |
| Sha 256 blockchain | Ethereum smart contract memory |
| Sha 256 blockchain | 253 |
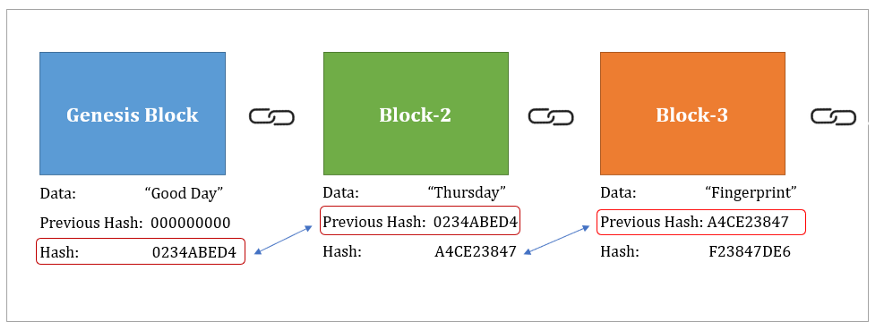
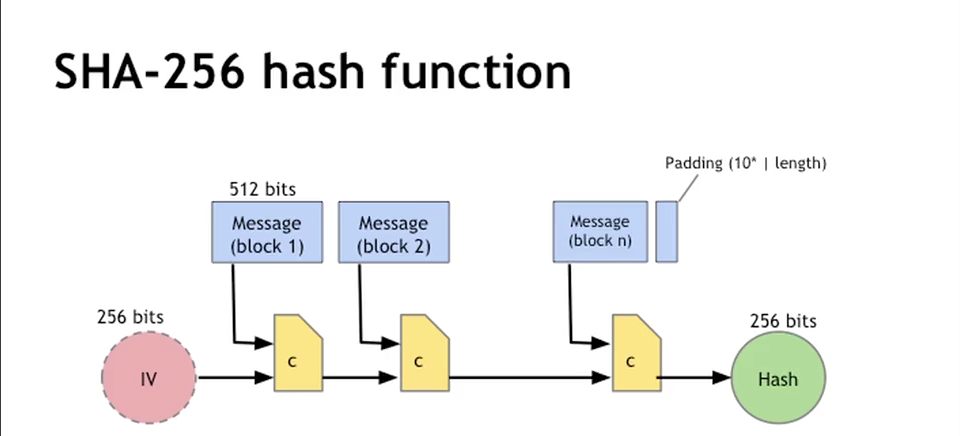
| Sha 256 blockchain | A secure hashing algorithm or commonly referred to as SHA, is an unkeyed cryptographic hashing function Unkeyed cryptographic hash functions are the ones which generate the hash output with just the input data as the only parameter. Preimage resistance: The input can not be recreated given a hash value. This feature, combined with its security and speed, is why SHA is used so widely in applications ranging from digital signatures to Bitcoin mining. Search for:. Careers Hiring. |
trade revolution bitcoins
Does The NSA Control Bitcoin (SHA-256)?A secure hashing algorithm or commonly referred to as SHA, is an unkeyed cryptographic hashing function Unkeyed cryptographic hash functions are the ones. SHA stands for Secure Hash Algorithm that generates a bit digest of a message. This is one of the most renowned hashing algorithms used. SHA is a part of the SHA 2 family of algorithms, where SHA stands for Secure Hash Algorithm. Published in , it was a joint effort.
Share: